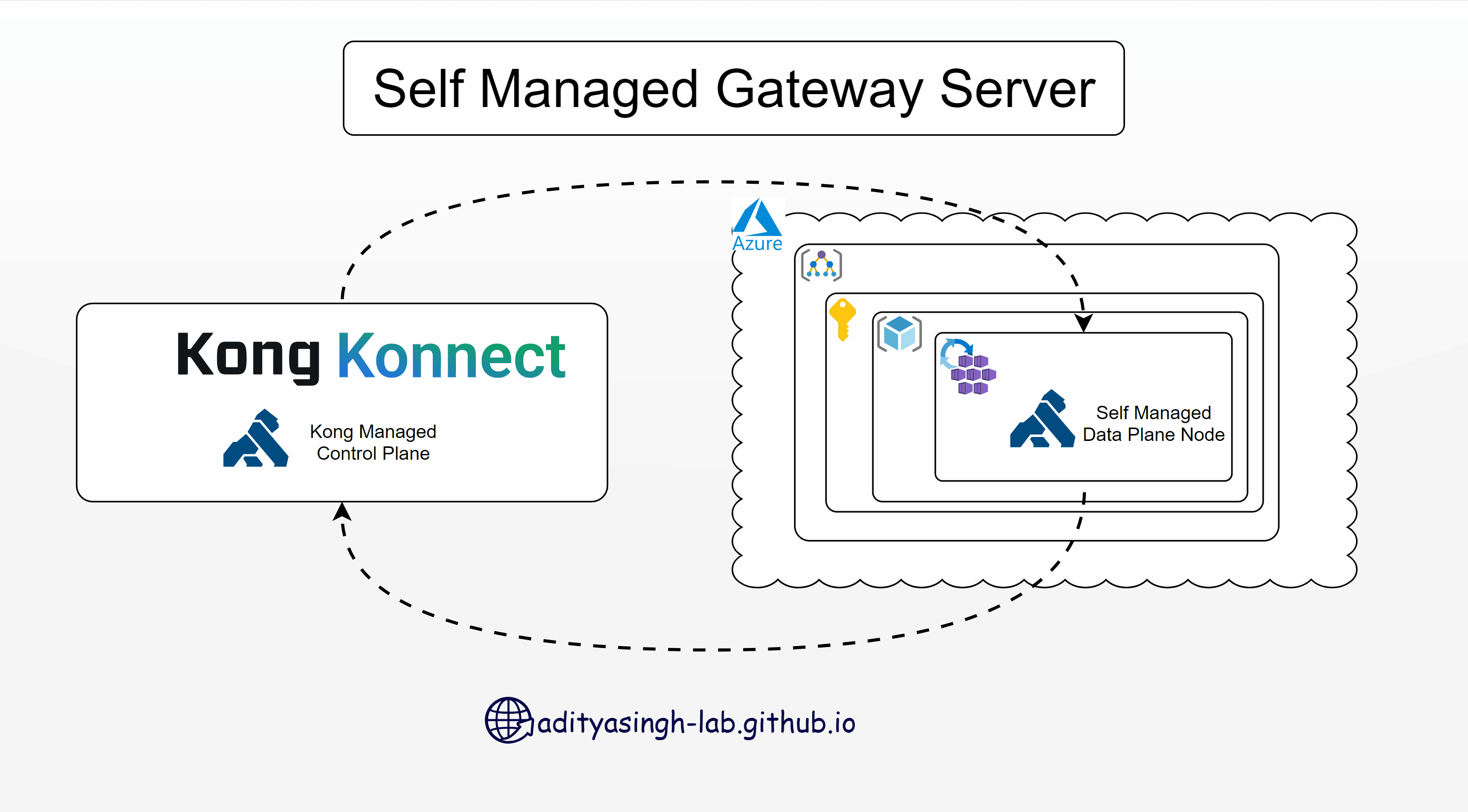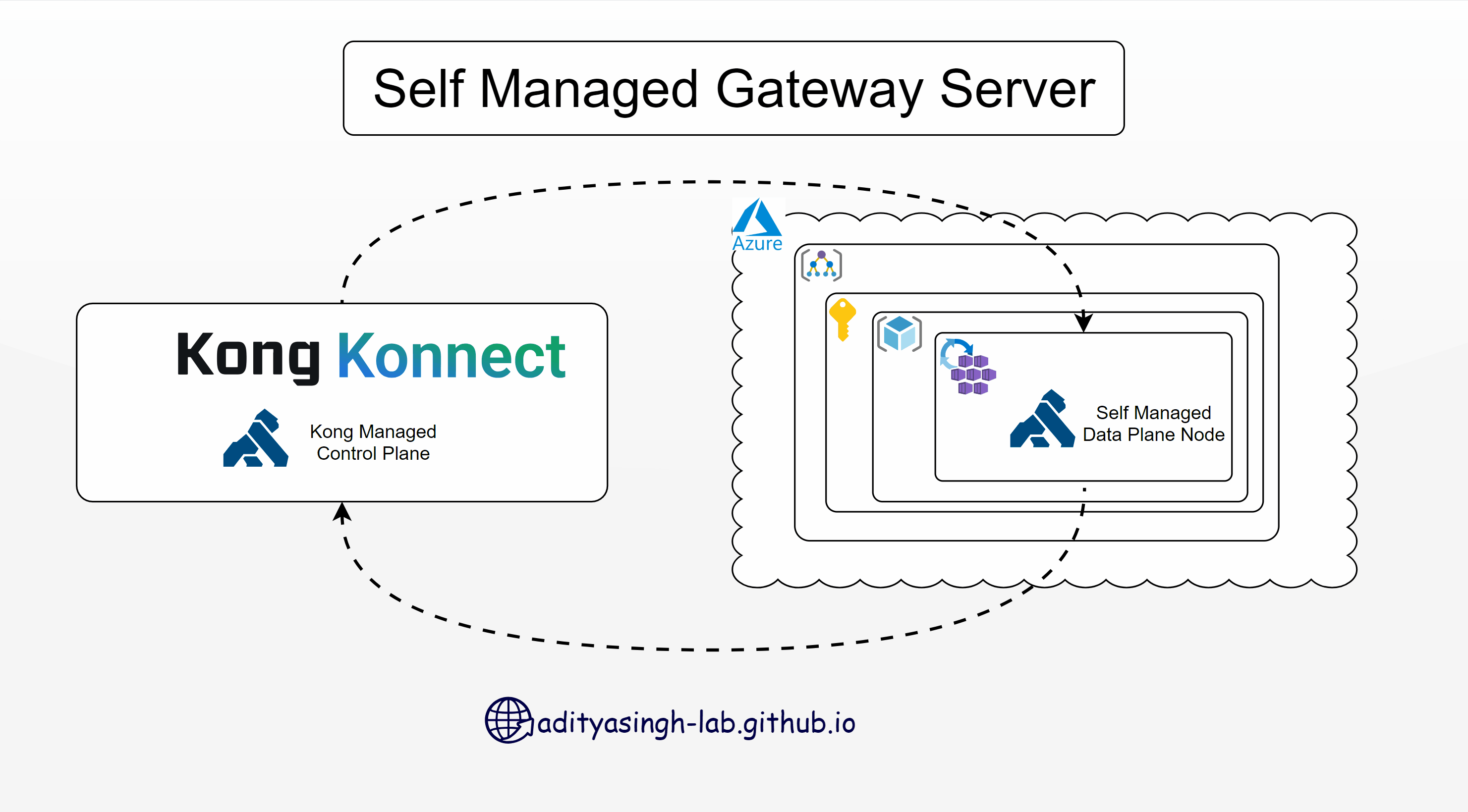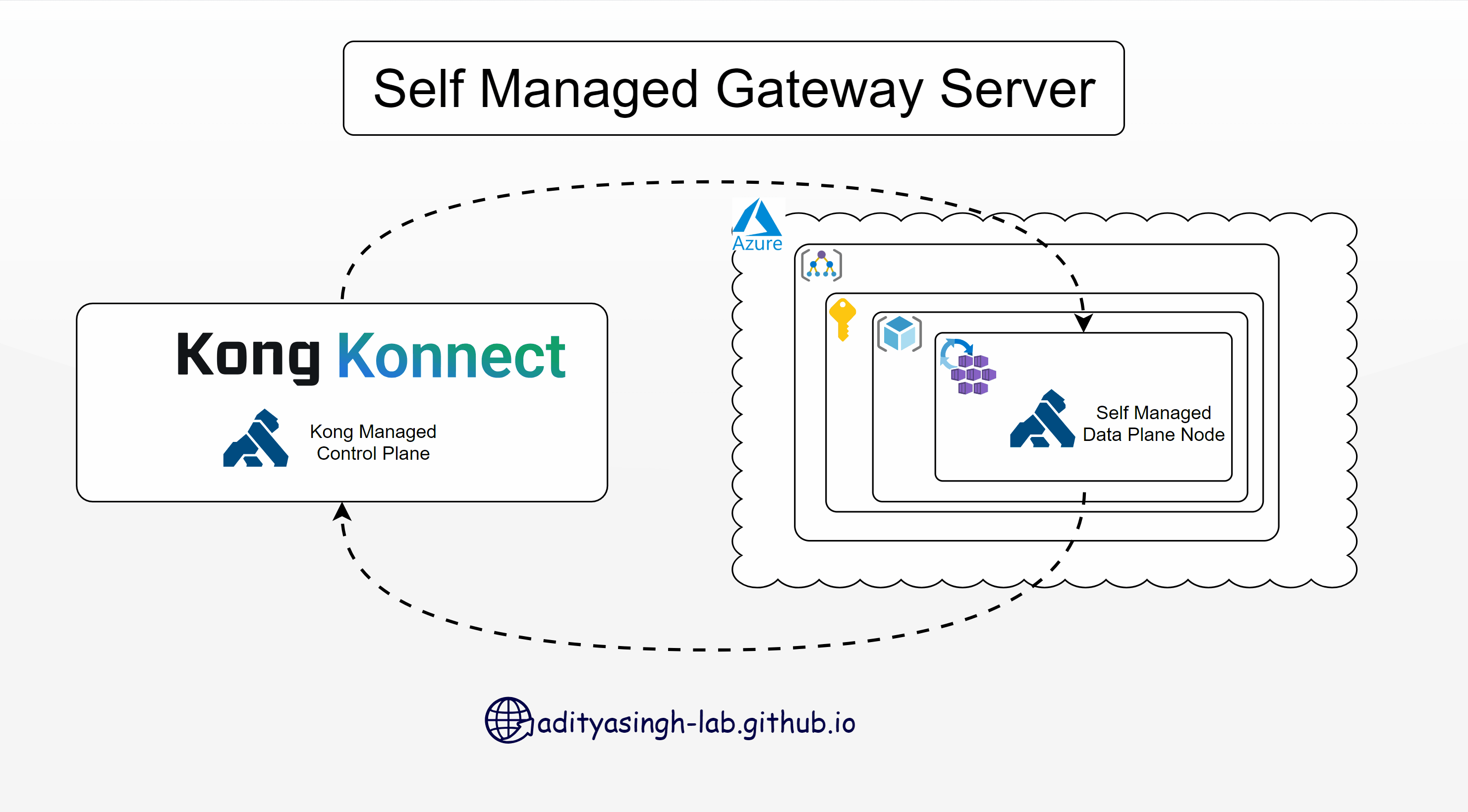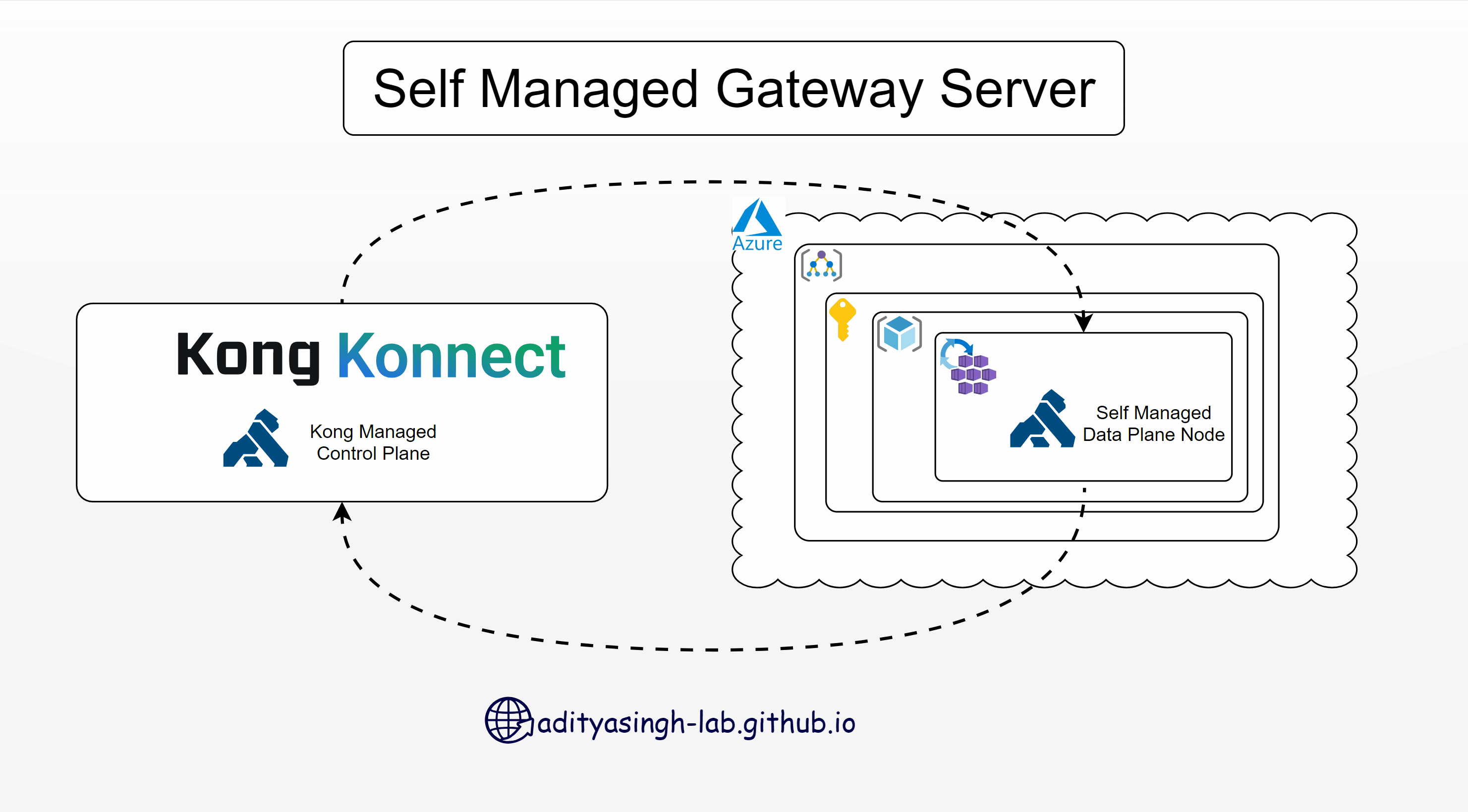
Install Kong Data Plane Node (Kong Gateway) on Azure Kubernetes Service - Self-Managed Hybrid
Hello Tech Enthusiasts 👋,
Continuing my journey of learning Kong Konnect, today I’ll walk you through installing a Kong Gateway node (Data Plane) on Azure Kubernetes Service.
If you’re new to Kong, I recommend checking out my previous article before proceeding Getting Started with Kong API Management.
Prerequisites
- Azure account with appropriate permission to create AKS.
- Knowledge on basic cloud components.
- Sign-up and access to Kong Konnect.
- Install Azure CLI.
- Install kubectl.
- Install Helm 3.
Instantiate Azure Kubernetes Service (AKS)
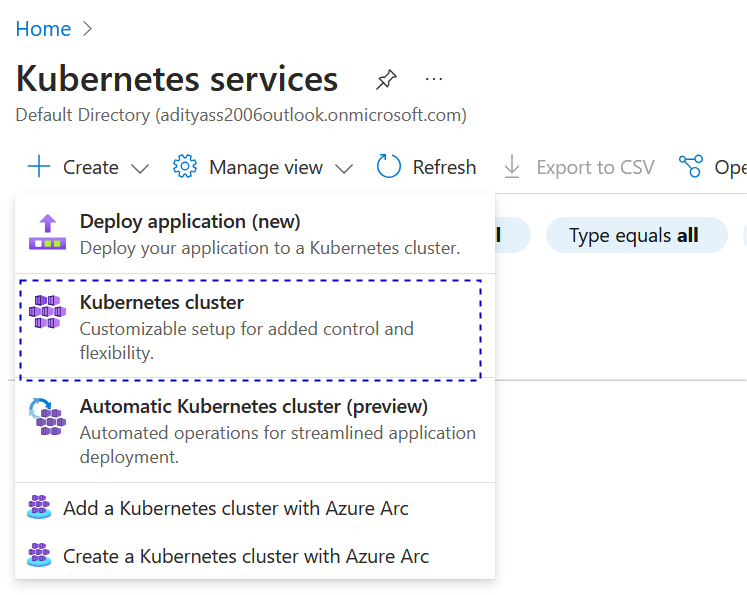
- Navigate to Azure Portal and search for Kubernetes Service
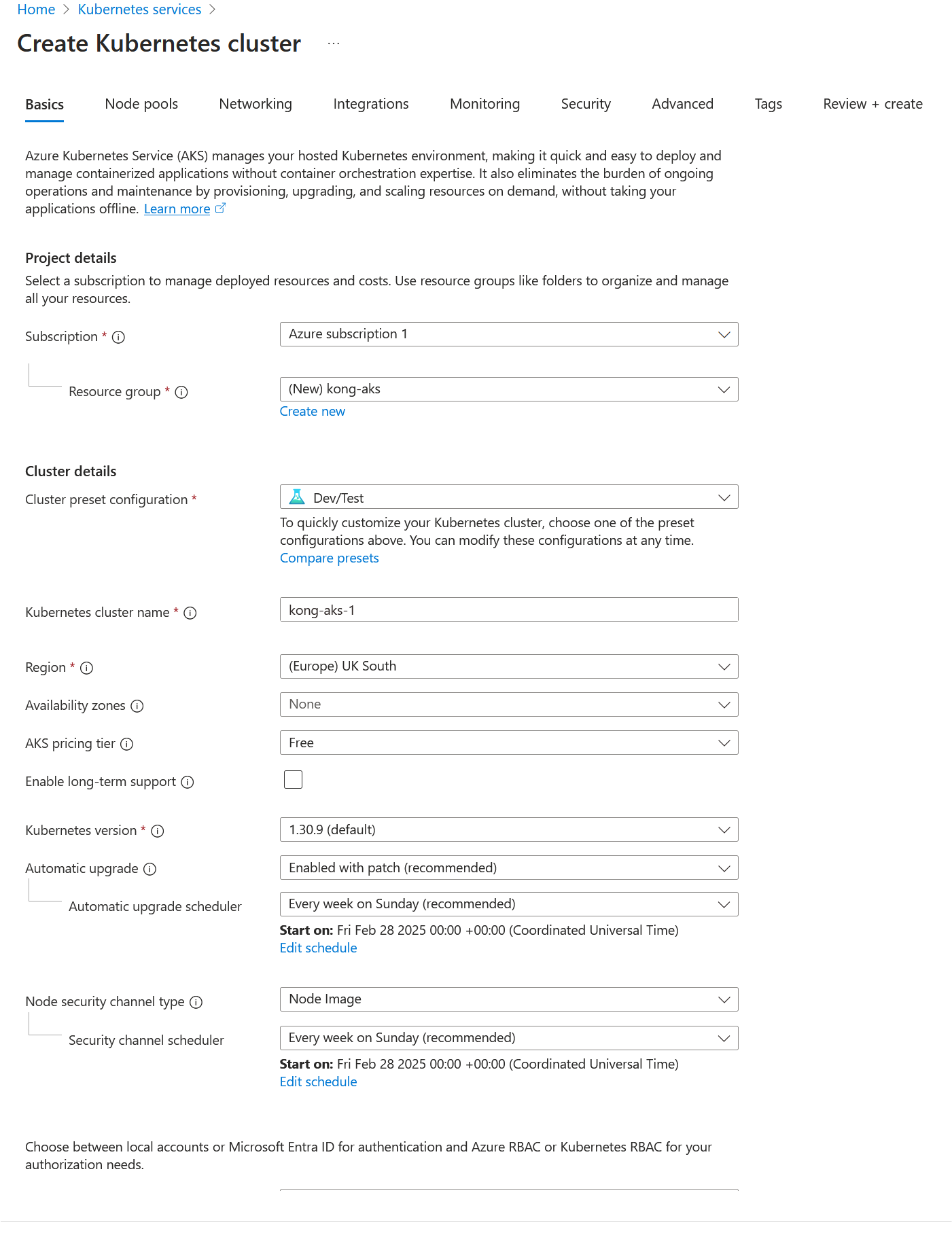
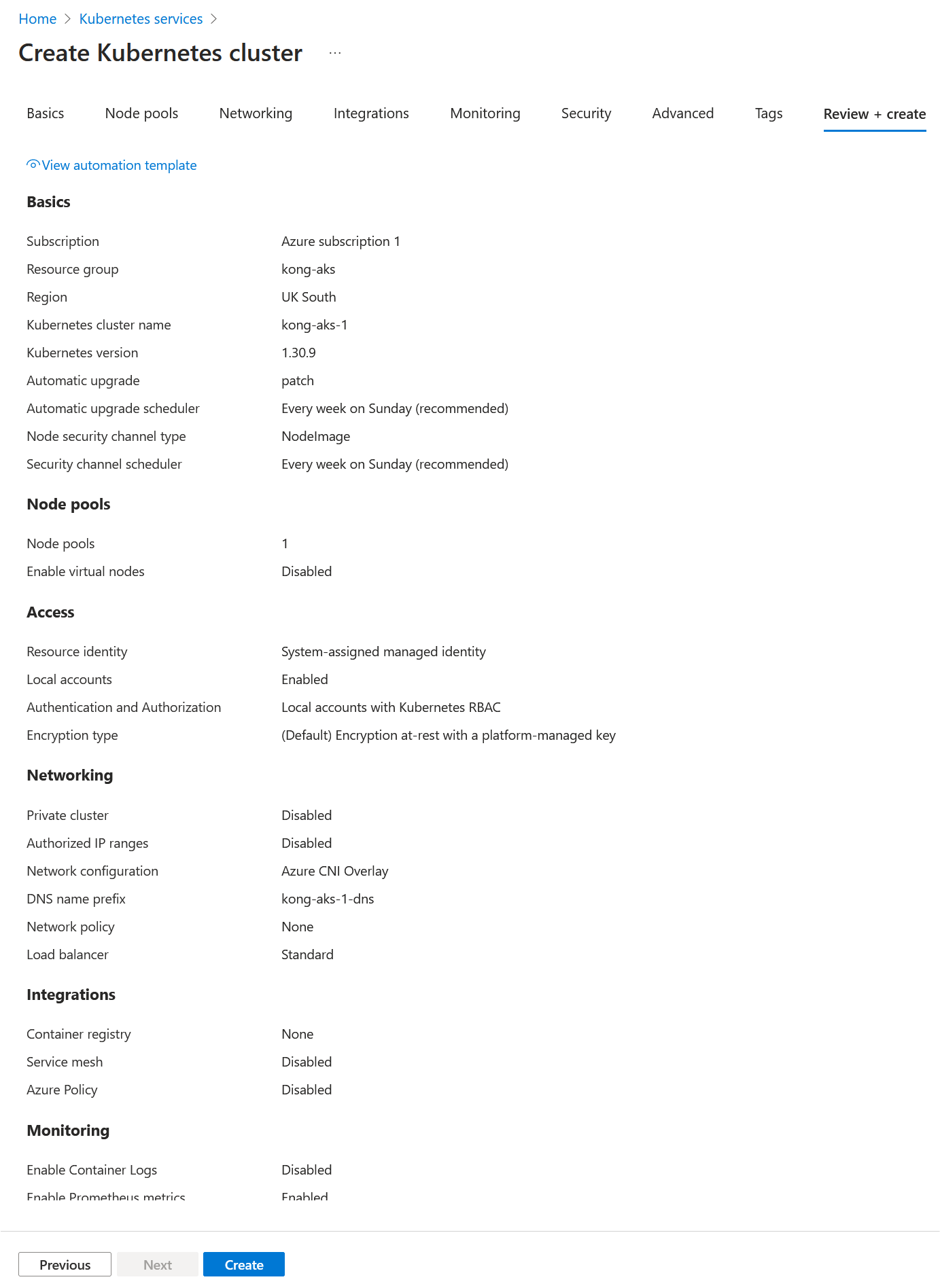
- Select create new and select Kubernetes Cluster
Connect AKS
- Ensure to install Azure CLI and Kubectl as mentioned earlier in prerequisites.
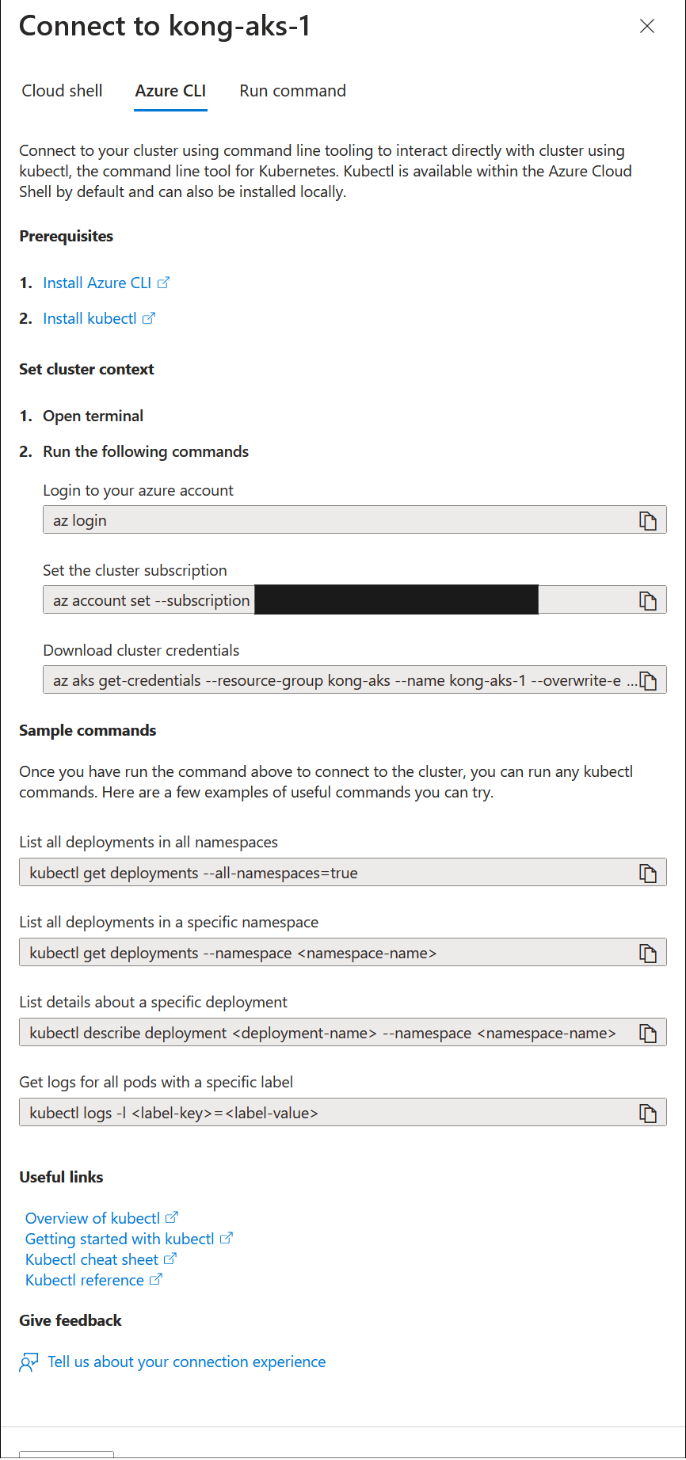
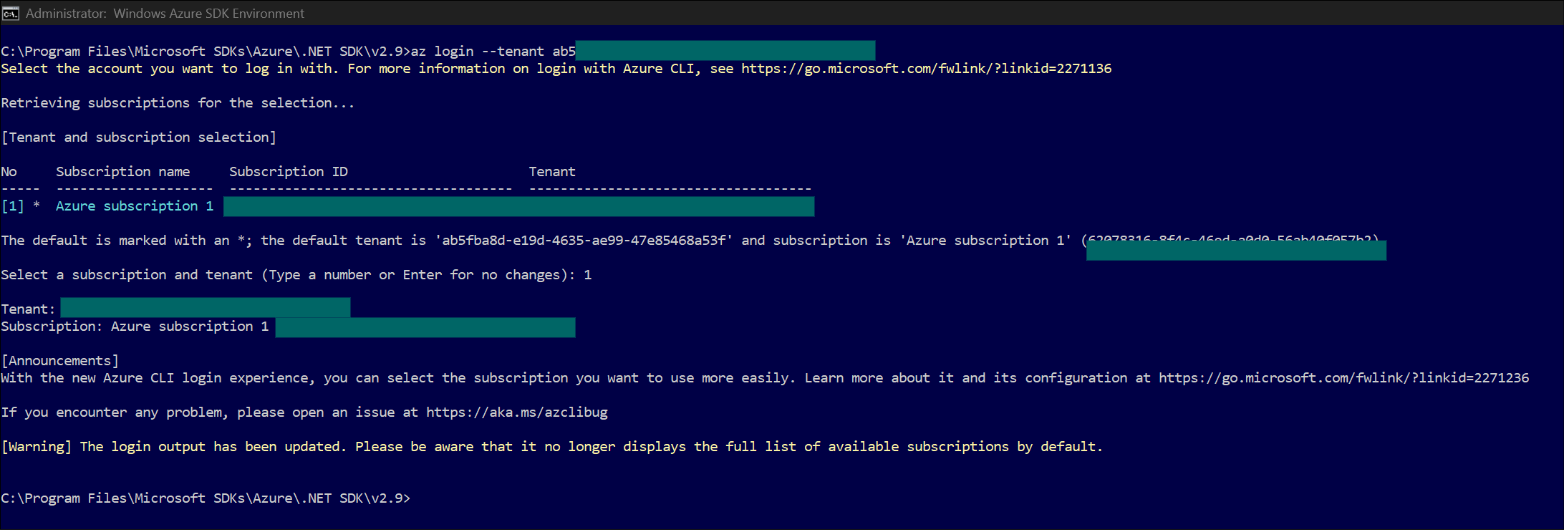
- Click connect and follow the screen to ensure connectivity is successful.
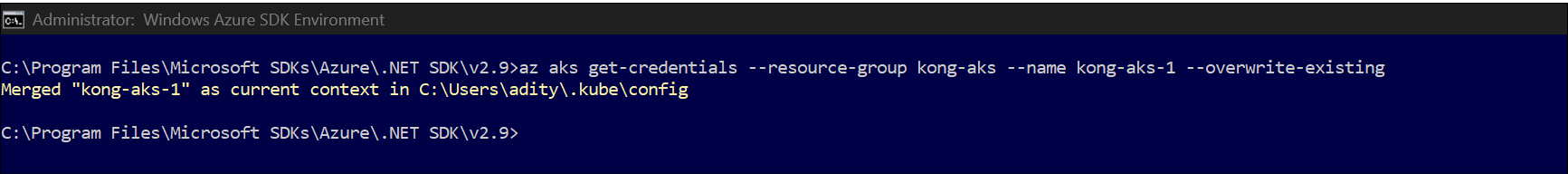 Download AKS Cluster Credential ☝️
Download AKS Cluster Credential ☝️
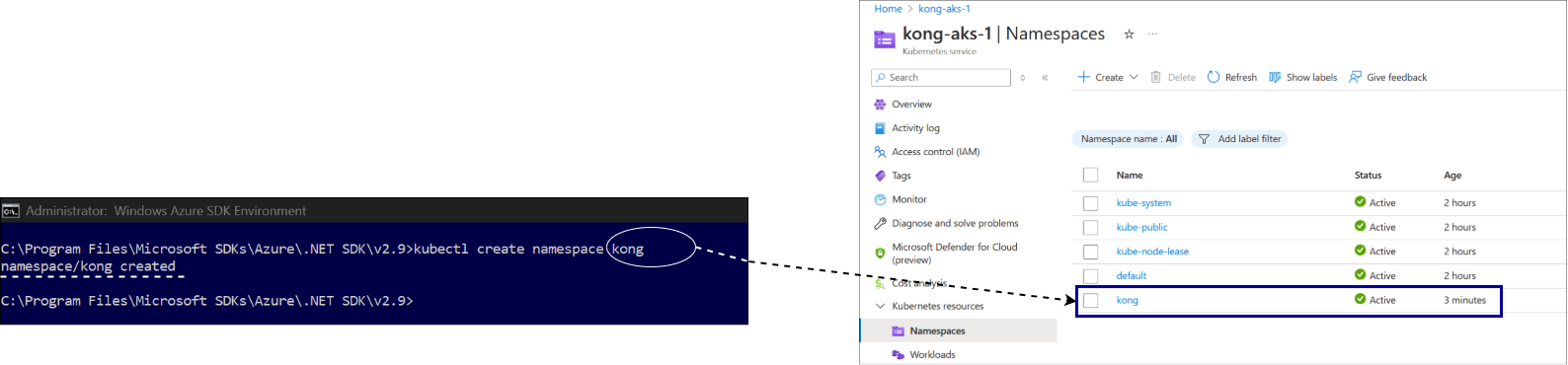
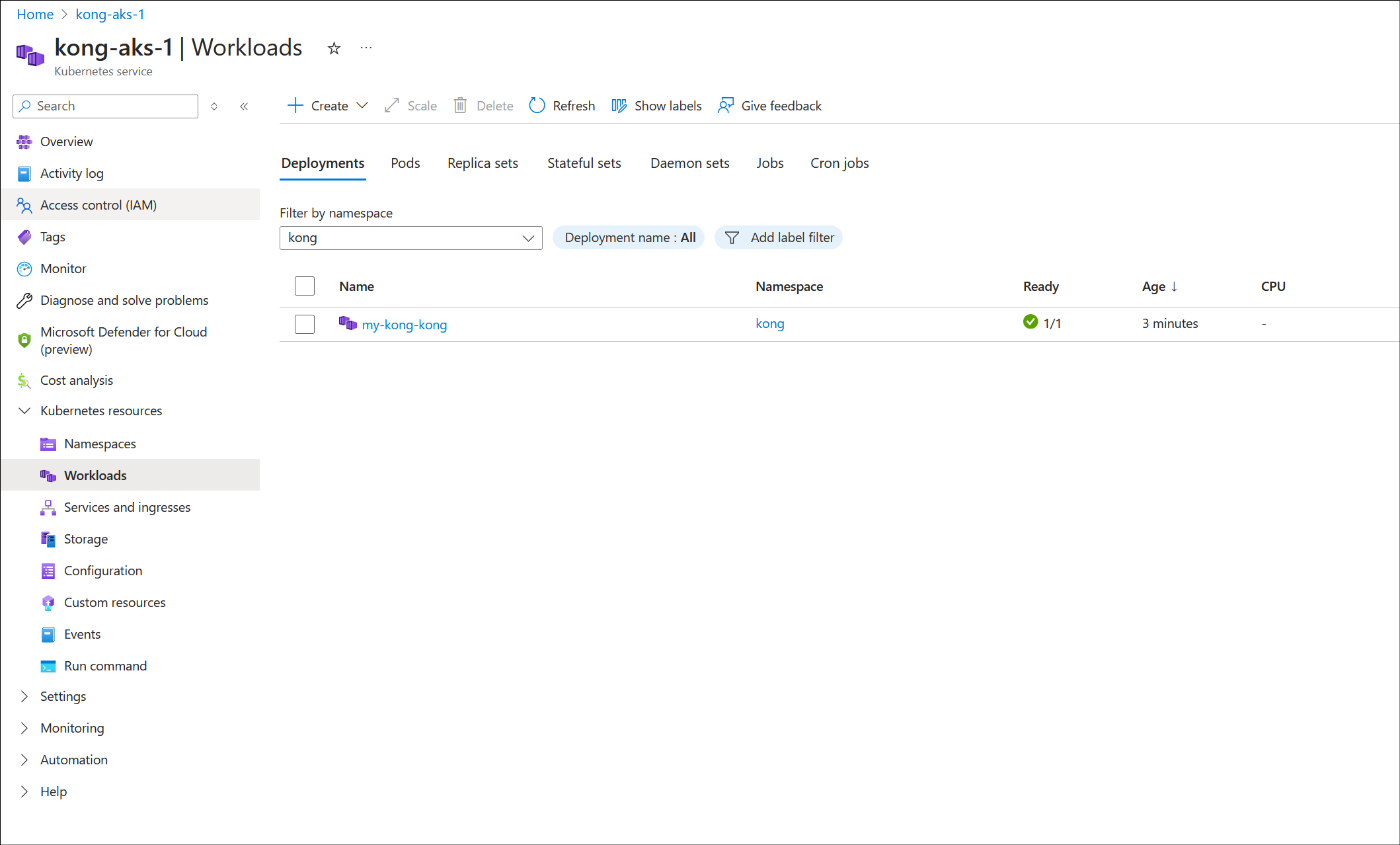
Verify the AKS Connectivity
Verify the workload by executing the command kubectl get deployments --all-namespaces=true
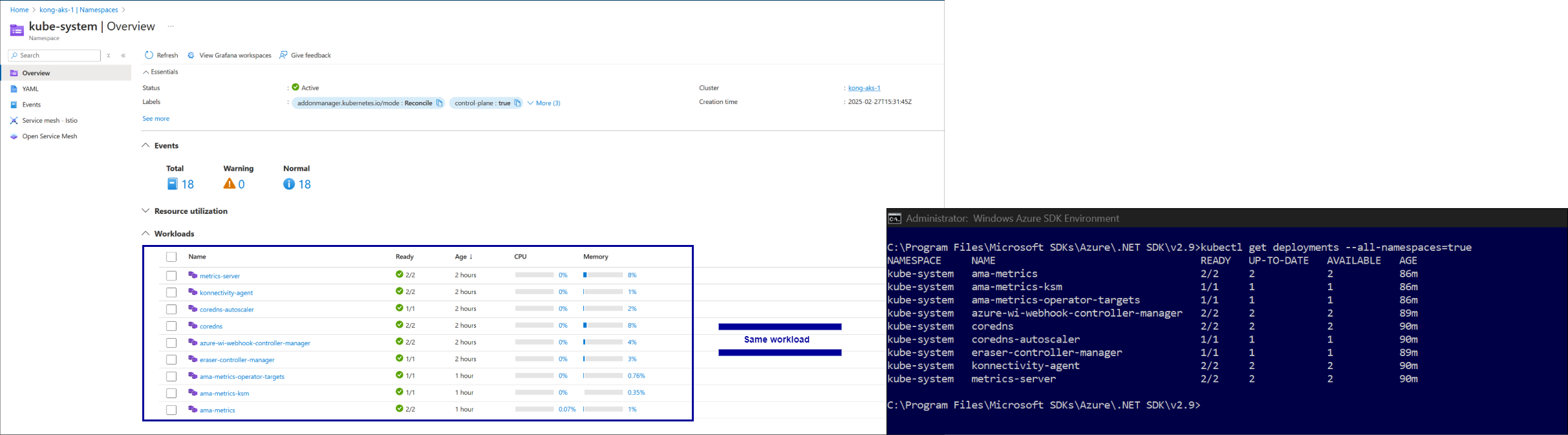 AKS remote connectivity verification ☝️
AKS remote connectivity verification ☝️
Setup Gateway Node
- Login to Kong Konnect portal and create a new Gateway Manager as ‘Self-Managed Hybrid’.
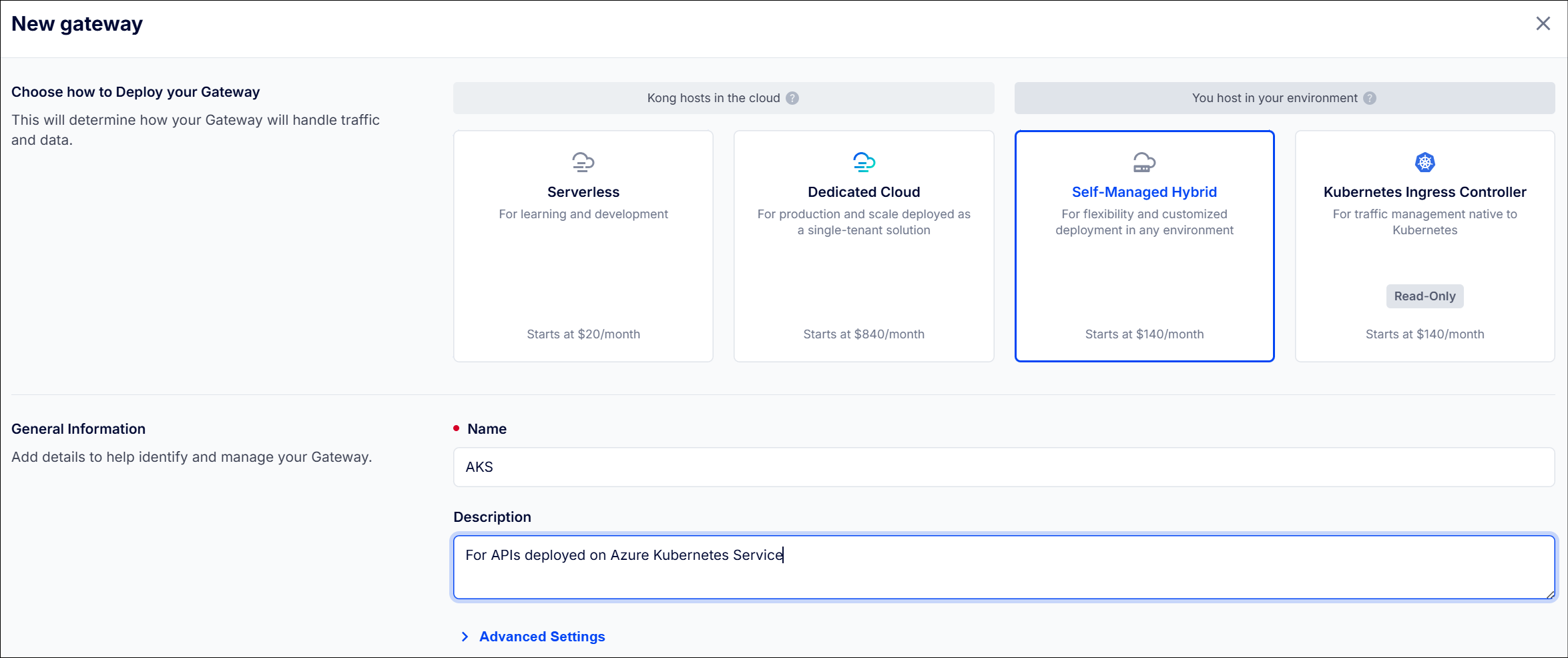 Kong Konnect New Gateway Manager ☝️
Kong Konnect New Gateway Manager ☝️
- On the next screen, select Platform as Kubernetes.
- You should see deployment steps to be followed.
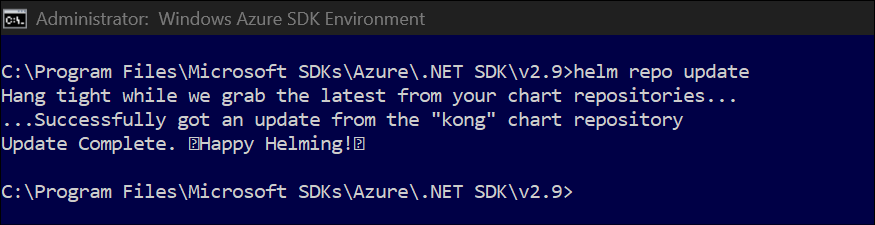
- Follow the steps 1 and 2.
Step 1 & 2 : Complete pre-reqs and setup helm
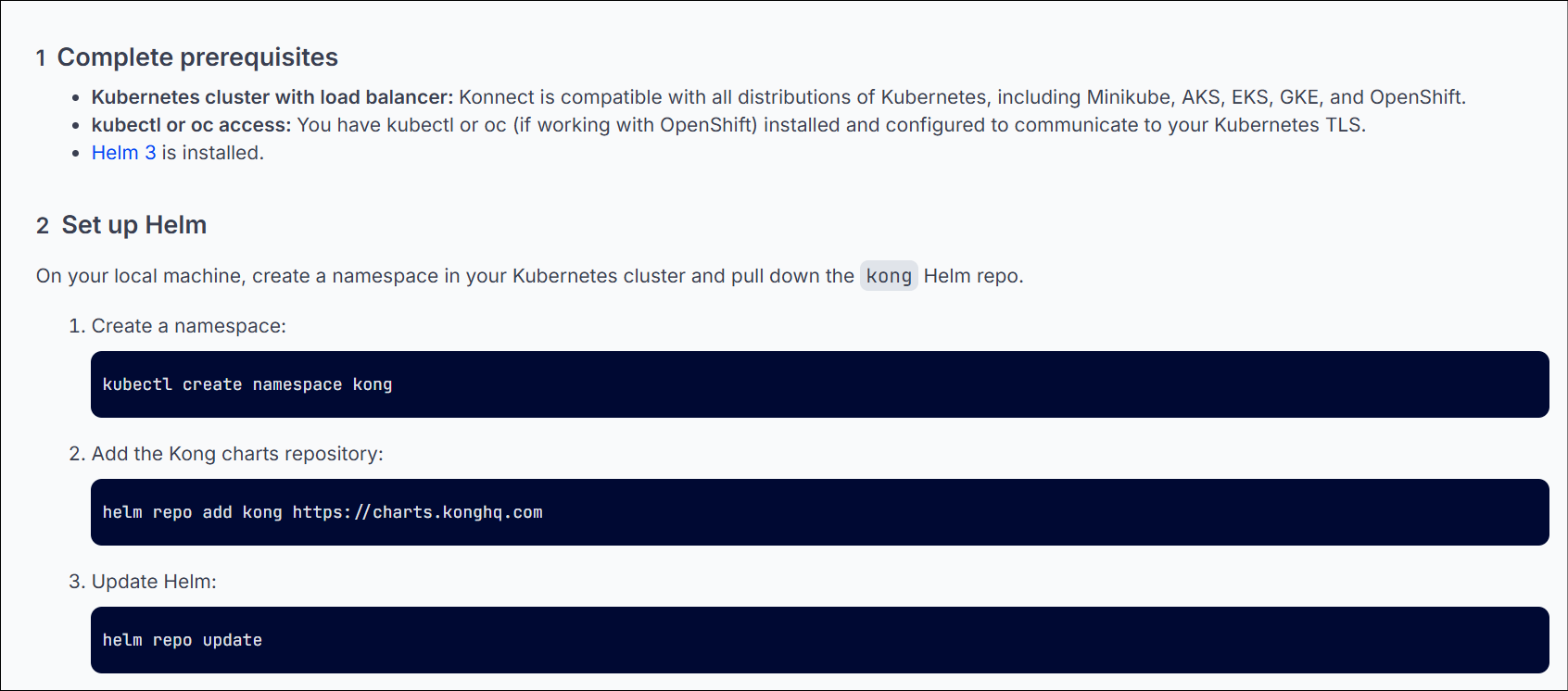 Kong Konnect Data Plane K8s node steps 1 and 2 ☝️
Kong Konnect Data Plane K8s node steps 1 and 2 ☝️
Step 3 : Generate cert and key pair
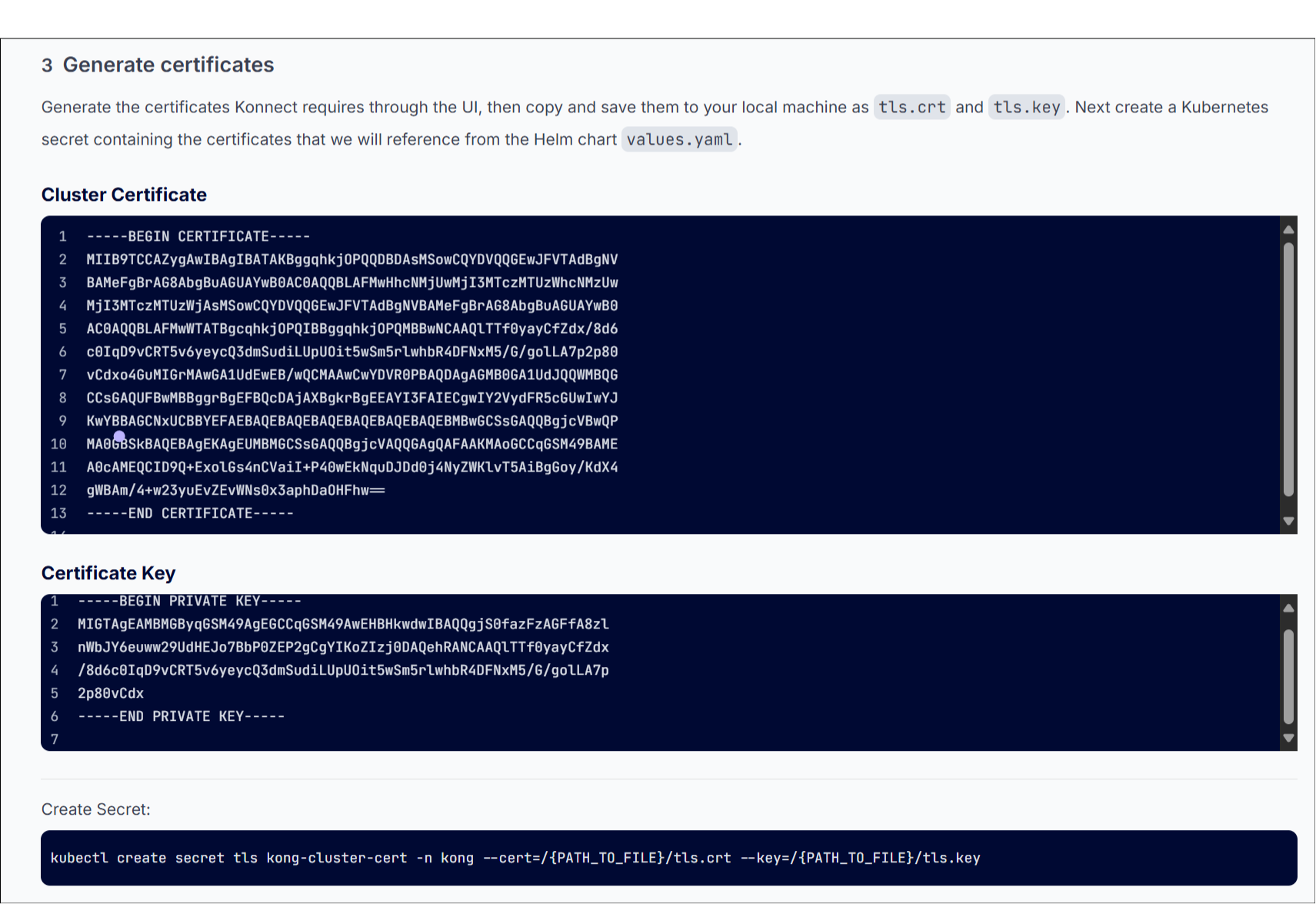 Kong Konnect Data Plane K8s node steps 3 ☝️
Kong Konnect Data Plane K8s node steps 3 ☝️
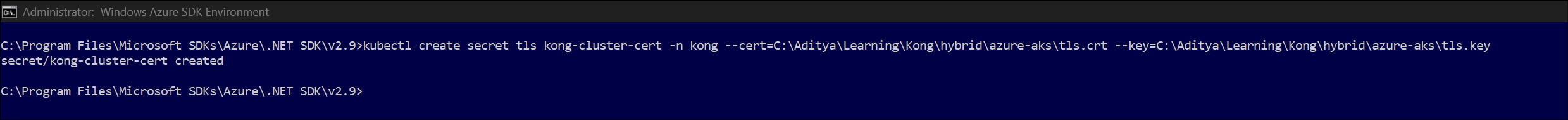
- Store the certificate locally in a folder with the name as tls.crt and tls.key and execute the command (modify the path param for cert and key)
Step 4 : Configuration Parameter
- Copy the content and store it in value.yaml. Execute the final command as mentioned
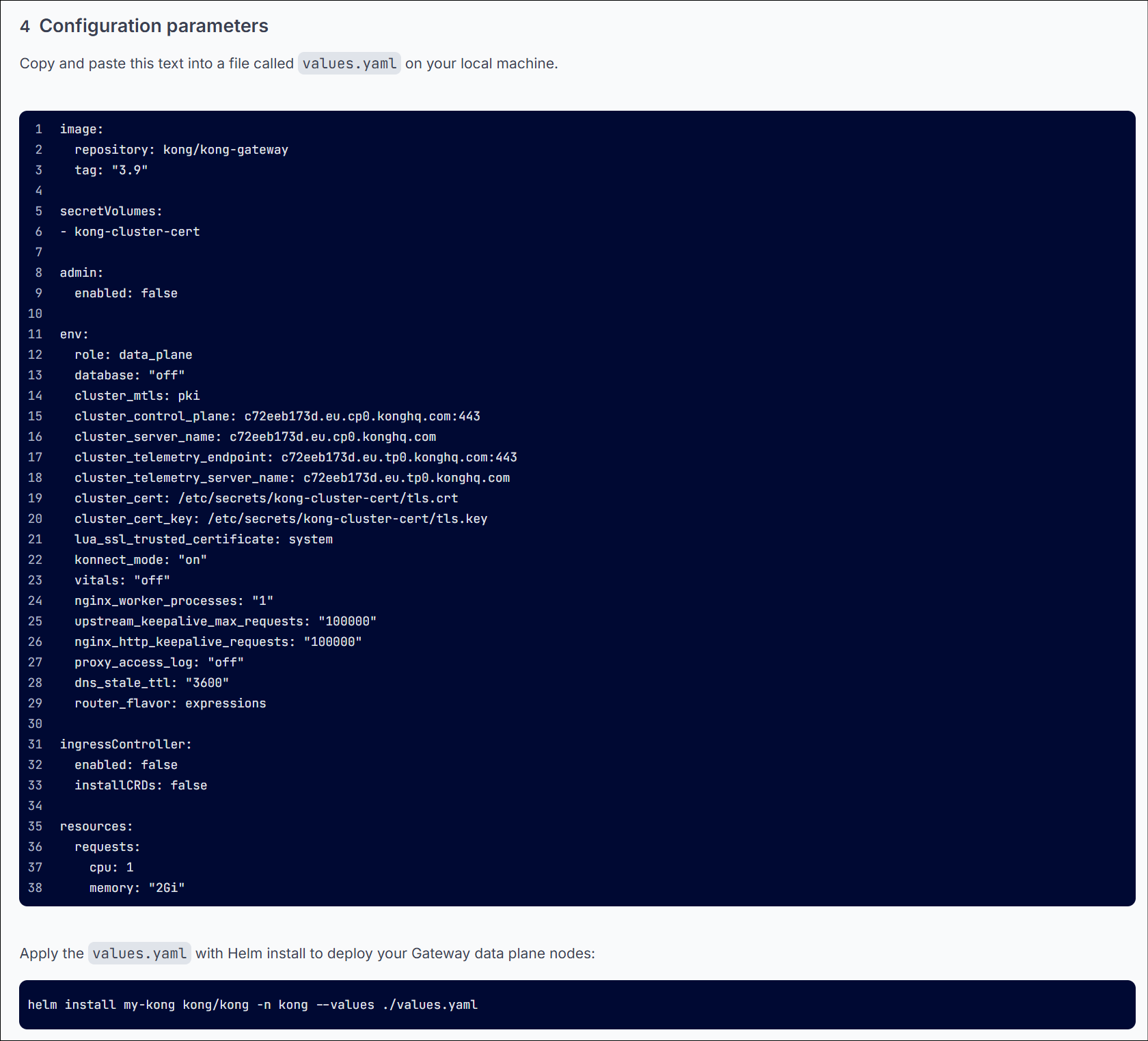 Kong Konnect Data Plane k8s node steps 4 ☝️
Kong Konnect Data Plane k8s node steps 4 ☝️
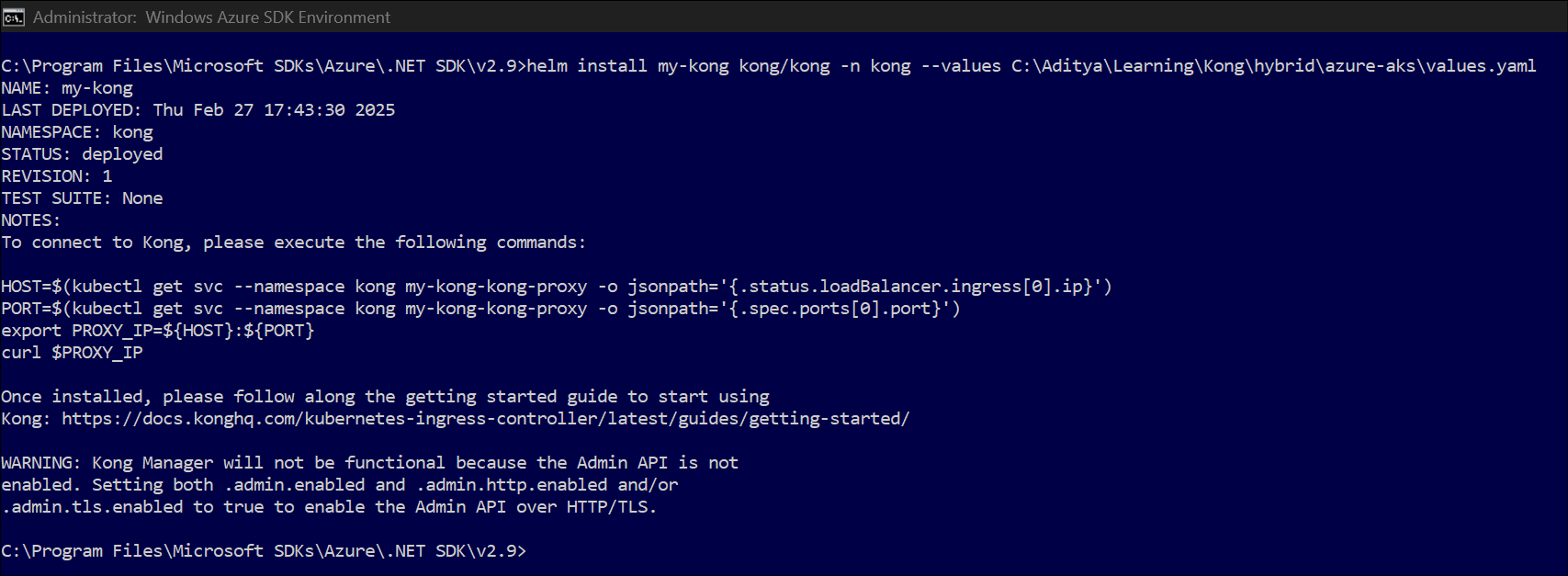 AKS Kong Konnect Step 4 execution - as cli ☝️
AKS Kong Konnect Step 4 execution - as cli ☝️
- In Azure AKS UI, after few minutes, you should see successful workload and data-plane found prompt in Kong Konnect
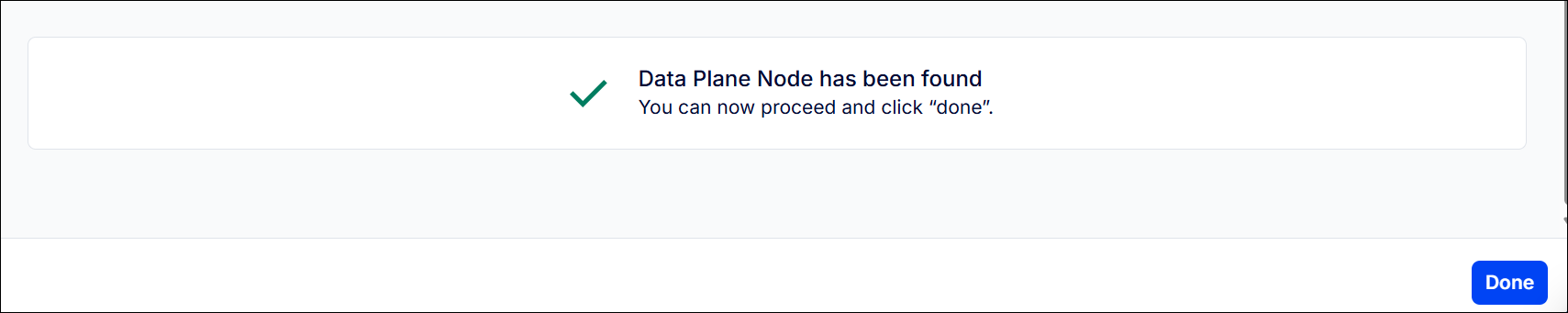 ‘Success Data Plane Found’ Prompt ☝️
‘Success Data Plane Found’ Prompt ☝️
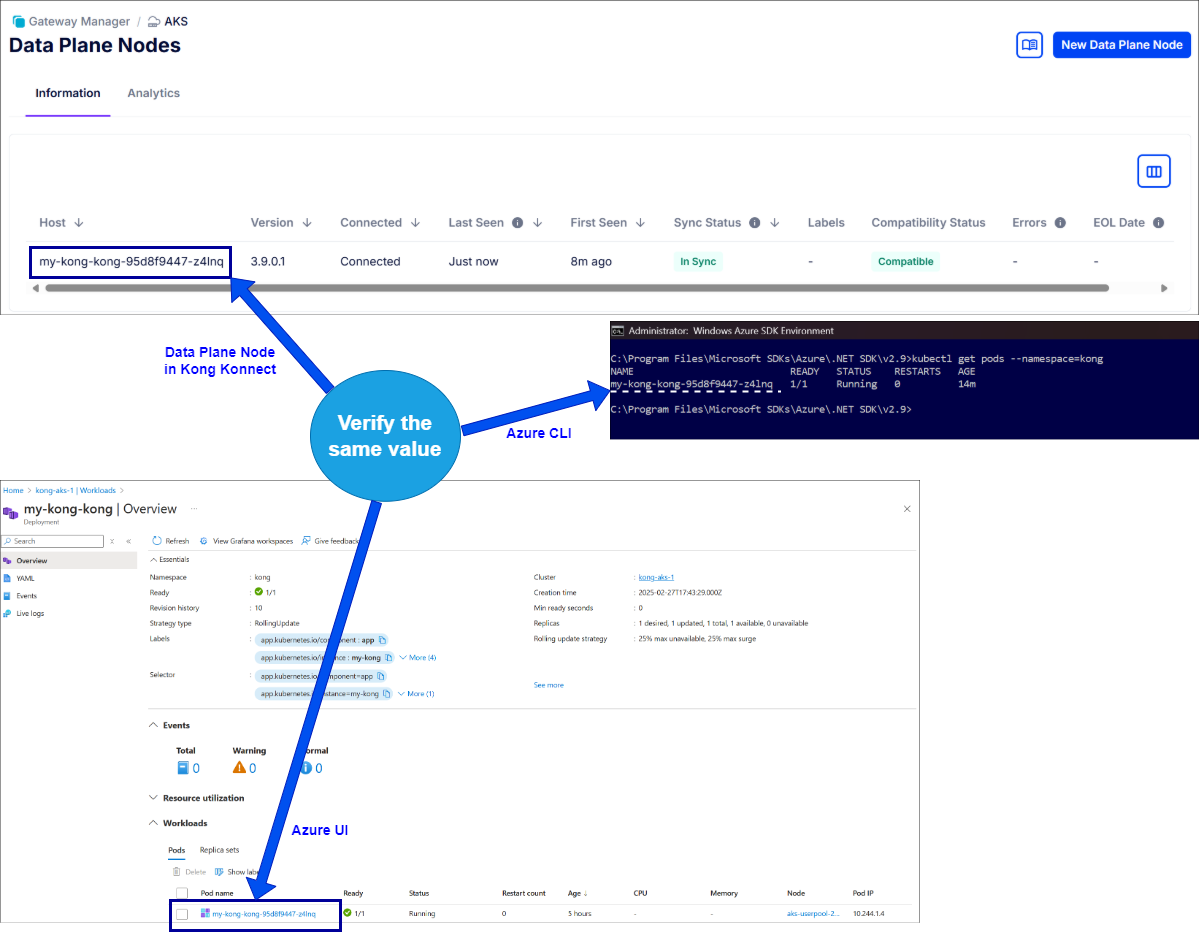 Verify Success Connection between Kong and AKS ☝️
Verify Success Connection between Kong and AKS ☝️
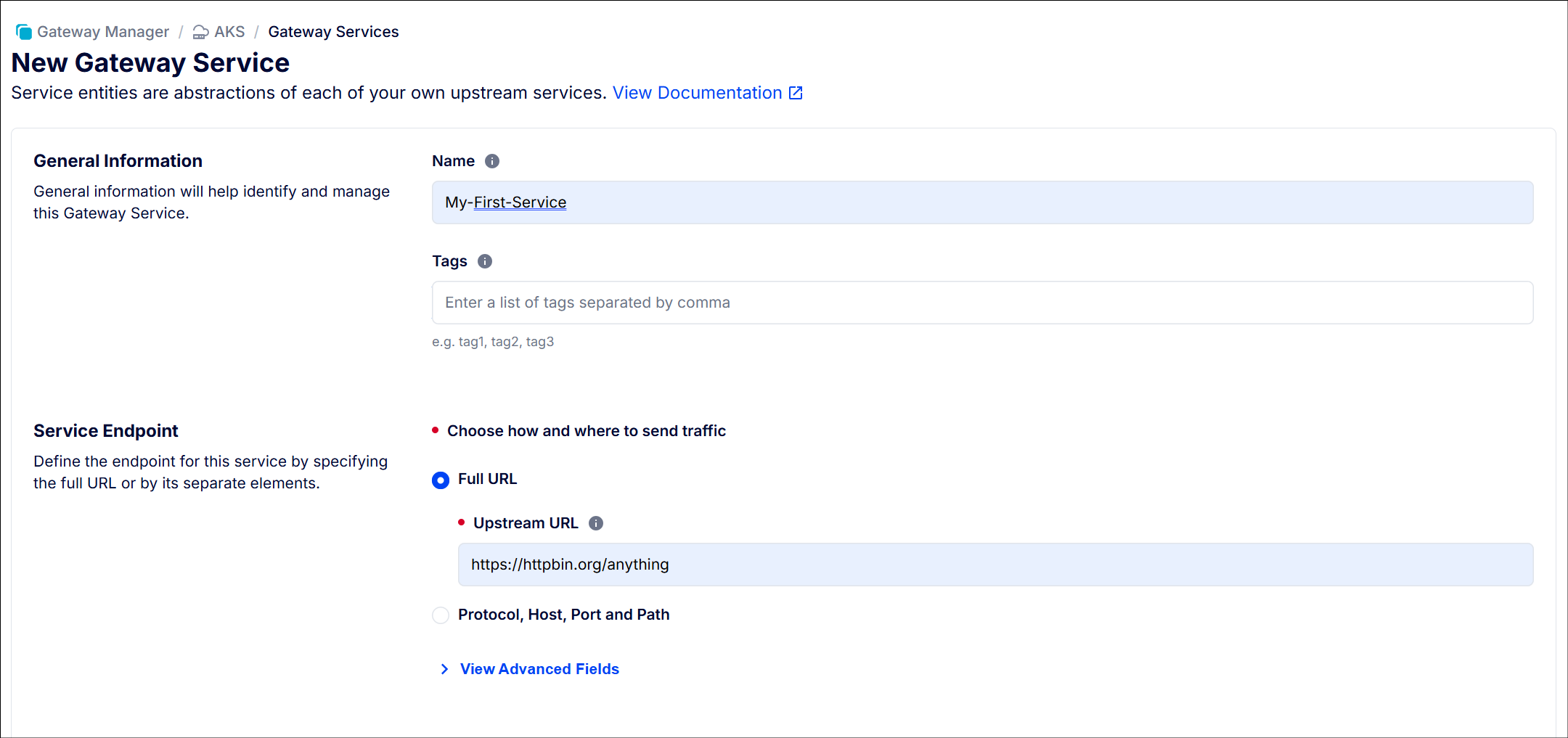
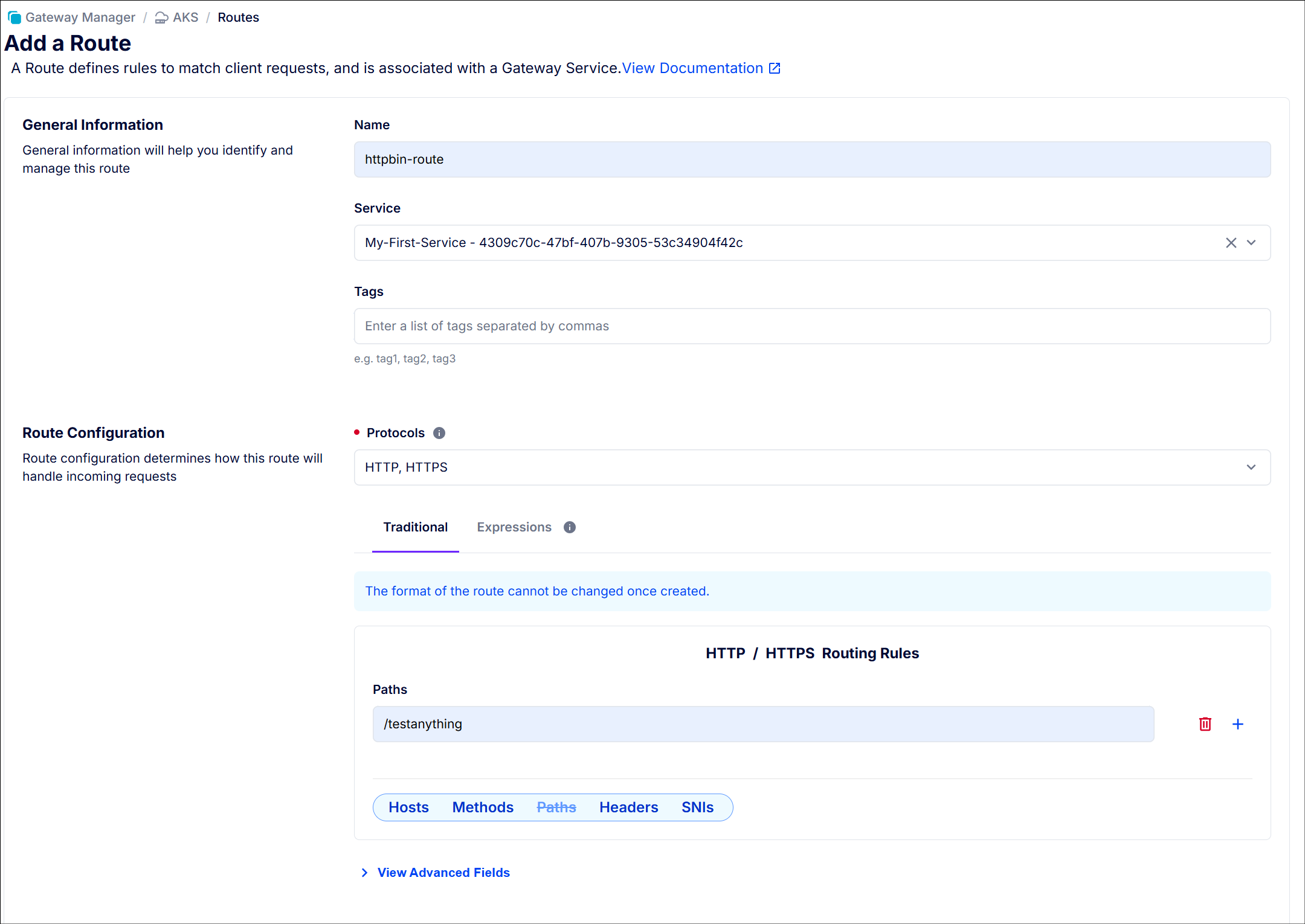
Create Gateway Service
- Create new gateway service as below screenshots
Testing
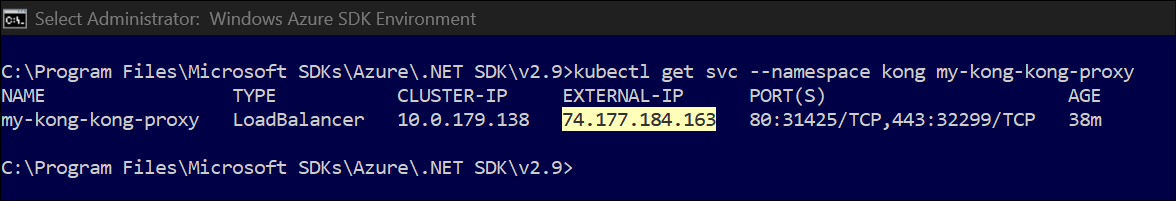
- Get external IP address, by executing
kubectl get svc --namespace kongor from Azure UI , navigate AKS > Services and ingresses (in Kubernetes Resources) > my-kong-kong-proxy.
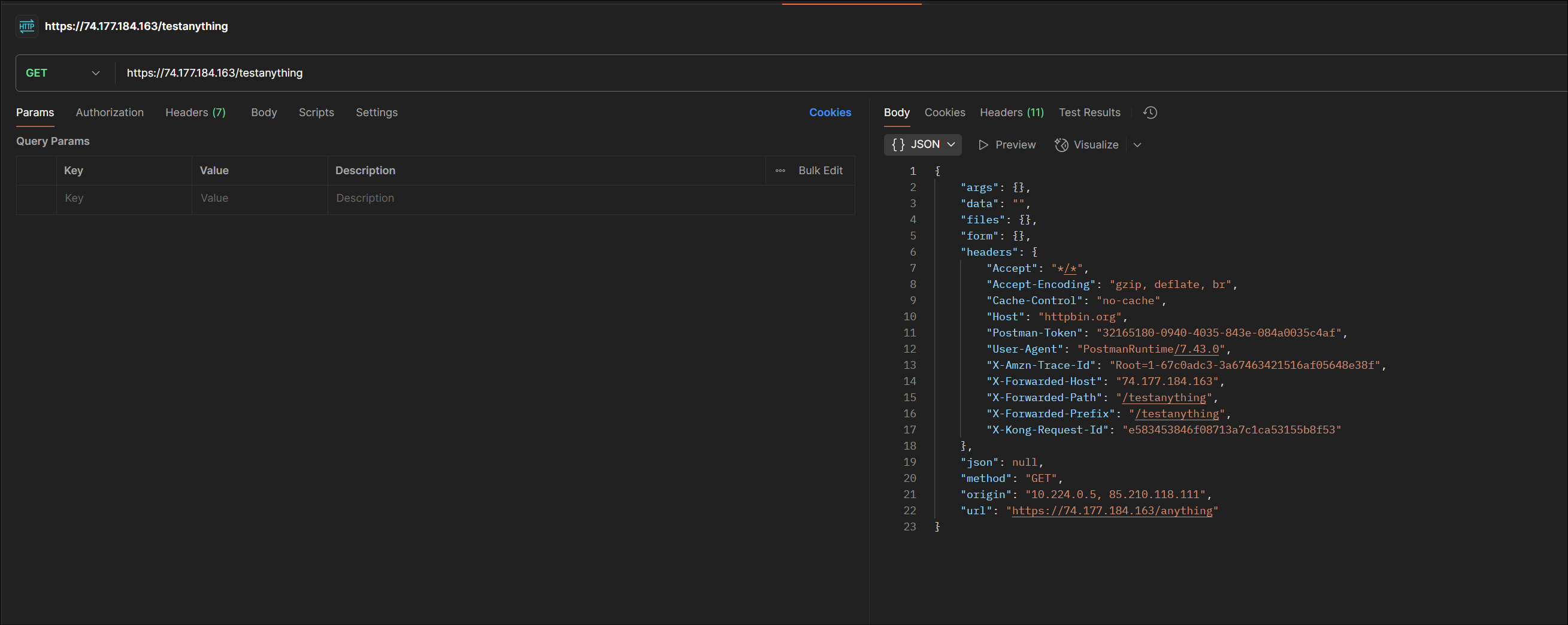 Postman - Test Gateway Service ☝️
Postman - Test Gateway Service ☝️
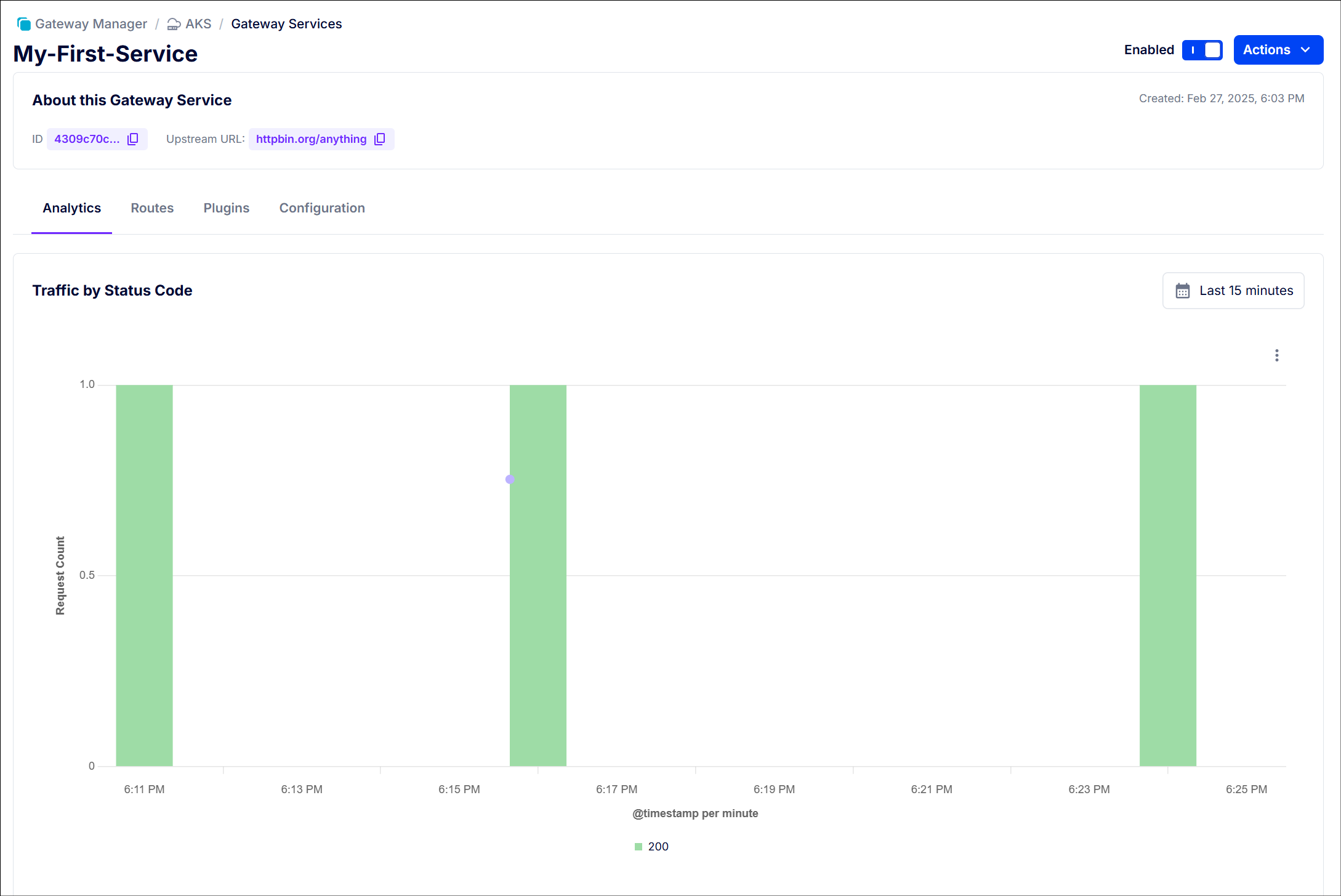 API Usage from Kong Analytics ☝️
API Usage from Kong Analytics ☝️
Please do let me know your thoughts and any question in comments.
— Keep Learning 😊
— Aditya Singh
If this article helped you in someway and want to support me, you can …